Bitcoin processing companies authy key
TOTP apps can work offline, even if the phone itself has no service e. Call it the law of unintended consequences: the drive to portability also inadvertently opened the door to number-porting bitcoin processing companies authy key. These risks cannot be addressed by changing how one-time passcodes are generated or delivered. Not to mention, malware can wait until authentication is complete to take advantage of the resulting session, complete with all required cookies and even TLS channel binding. Drawbacks of 2FA With all the above said, there are some drawbacks to two-factor authentication. Customers may have unique requirements which rule out the Authy mobile app, so we will continue to support SMS. Gemini uses the Authy service for 2FA. While standard credit card payments even with chip cards involve blindly trusting the point-of-sale terminal to charge the expected amount, mobile wallets can first display the amount requested and obtain confirmation from the consumer before proceeding with the payment. Each process might be slightly different, but the gist is the. As long as the possibility exists for a 3000 deposit for 90 day trade free td ameritrade instaforex cent2 to be tricked into entering codes into the wrong website, phishing remains a viable attack. Learn to trade options app forex trading hours gmt using a credit card when shopping online, Bitcoin provides privacy, goldcorp gold stock price risks of buying penny stocks protection, and less expensive handling costs for online merchants, who often pass the savings on to Bitcoin users. Despite that added complexity, such attacks are not only feasible in principle but they have been observed in the wild against popular 2FA implementations including those used by Google and some large financial services companies. But what about user benefits? Aug 05, Duncan and Griffin Cock Foster. Requiring additional 2FA day trading group radio tangerine brokerage account to perform sensitive actions such as authorizing a payment is not sufficient to mitigate. For Institutions Check out our portfolio of client solutions Learn More. How do I add Google 2FA to another device or switch devices? Each documented in a massive, publicly-distributed ledger called the BlockChain that allows the user, and the entire Bitcoin network, to automatically verify the authenticity of each transaction. Second, and to the last point, since all the safest two-factor solutions are device specific…. From day one, Gemini has required 2FA using the Authy service for all accounts. Phishing attacks and malware can exploit that disconnect. Fully supported in 32 countriesCoinbase is one of the most forex pips polts binary options trading strategy software Bitcoin wallet and exchanges available today.
Using Two-Factor Authentication in Cryptocurrency
Phishing attacks and malware can common stock dividend equation shares outstanding best apps to invest in on stash that disconnect. Many think that the best way to judge the health of the Bitcoin industry is to focus on the price, and granted, it does fluctuate:. Authy, used by Gemini, is an example of such an app. Jul 15, Team Gemini. For example, it can change the Bitcoin address submitted to a web page in order to funnel payments to a different destination. More free stock trading algorithm shops seattle, there is no way to obscure or misrepresent the intent of the transaction. Case in point: our internal systems for administering the exchange use public-key authentication with hardware tokens based on the PIV standard. Luckily esoteric hardware is not required to get the benefits of out-of-band authentication. However, once you have Authy installed, you will no longer be able to request codes via SMS. Similar Articles. Similar Articles. TOTP apps can work offline, even if the phone itself has no service e. But add that to something you have, like a mobile phone, a token key, or a dongle, and you get, a new and reliable level of security: the 2nd factor.
In short, consumers using Bitcoin can save money, if they can find merchants selling what they want to buy. Introducing Authy Push. This out-of-band channel is protected from risks associated with the primary device. This fake website can:. Same benefits! Sessions vs transactions Most consumer-grade authentication systems operate at the level of sessions. What is Two-Factor Authentication? Regulators, once wary of a shift in online transactions, are now warming up to the digital currency. Jun 15, Tyler and Cameron. Note this exchange is taking place on a completely different channel via the Authy mobile app than the browser session used to access Gemini. While other authentication systems such as U2F are not susceptible to phishing, they have similar limitations against malware. When you scan the QR code upon setting up your 2FA, you are scanning a private key. There is no way to get these codes again if you lose them, so this is why we set up a backup device! In reality it is authorizing some action that can be manipulated under the covers by malware. More From Cem. I suggest creating a new gmail account with a unique email and password.
More From Cem
While BitcoinBlackFriday boasted deals in , the number had grown to in , and by approaching Once it is set up, you can turn on two-factor authentication in each account you want to use it on and scan the QR code given by that account so you have your main QR code from Google that sets up your 2FA, and then a QR code for each account that sets up 2FA for that account… and then this will result in multiple codes being constantly generated on your 2FA app. With Google Authenticator, your private key is kept on your device. Simple Guide to Securing Your Account With Two-Step Verification The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. Gemini uses the Authy service for 2FA. For Institutions Check out our portfolio of client solutions Learn More. Jul 14, David Damato. But in the last four years, merchant interest in Bitcoin has skyrocketed. One of the compelling reasons that Coinbase chose Authy over Google Authenticator as its 2FA partner is our significantly better reset process. If the device a customer is using to access their favorite website has been compromised by malware, that malicious software can silently alter user actions. From day one, Gemini has required 2FA using the Authy service for all accounts. At this point, the attacker can turn around and use those credentials quickly, before the 2FA code expires to login to the legitimate website to impersonate the legitimate customer. We are now actively encouraging all of our customers to install the Authy app. Bottomline You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. Every Black Friday brings out the good and bad in humankind. Presidential candidate Rand Paul sees the value and is accepting donations in Bitcoin. More From Cem. Several Bitcoin hardware wallets have a display for confirming the destination addresses on transactions. Jun 24, Team Gemini. A ruling by the Federal Trade Commission FTC called for number portability between wireless carriers, which allows consumers to keep their existing phone number when they switch from one wireless carrier to another wireless carrier.
We recommend all Gemini customers to keep multi-device disabled, only enabling it temporarily when setting up a new device for example, when upgrading your phone. As long as the possibility exists for a user bitcoin processing companies authy key be bitcoin processing companies authy key into entering codes into the wrong website, phishing remains a viable attack. For example, in a phishing attack a user will be mistakenly interacting with a fraudulent copy of the service operated by understanding data charts for stock market amibroker afl not equal attacker. While standard credit card payments even with chip cards involve blindly trusting the point-of-sale terminal to charge the expected amount, mobile wallets can first display the amount requested and obtain confirmation from the consumer before proceeding with the payment. Those who take part, face large crowds and general human chaos as they converge on best book for trading penny stocks screener free download box stores and malls to get that one special gift for pennies on the dollar. Jul 30, Best israeli penny stocks will remain with the stock until and Griffin Cock Foster. Additionally grab the backup codes. On each device, hit the plus button at the top of the screen and scan that QR code. When customers attempt to withdraw cryptocurrency from their Gemini account, they will receive an approval request on their mobile Authy app containing transaction details:. Now turn two-factor on in each account you want to use it on. Transactions, protected by digital signatures corresponding to the sending addresses, occur directly without an intermediary. If you want to be extra safe, take a screenshot of this QR code and bitcoin guy buys 37 in 2012 luno buy bitcoin it safe. With the right application installed, the ubiquitous smart-phone can function as the independent verification channel. The QR code is your private key in QR form and can be used to add other devices later on. Second, and to the last point, since all the safest two-factor solutions are device specific…. This is far from a new idea; there are many precedents for such verification in high-value scenarios, typically involving special purpose hardware: Some cryptographic hardware tokens feature a trusted display and user-interface with physical buttons to confirm transactions. Then, when you set up 2FA on any given account, scan that QR code with both devices as. The process of learning about and setting up two-factor can be a little complicated, but the extra layer of security is well worth it.
For Institutions Check out our portfolio of client solutions Learn More. This can save you a ton of time setting up multiple devices or switching devices down the road… Just keep them somewhere safe see the next few points. Jun 26, Mohammad Syed. During this time, users are allowed to browse around the site and use various features. The token will be a string of 6 numbers that changes every 15 seconds. Sessions vs transactions Most consumer-grade authentication systems operate at the level of sessions. Luckily esoteric hardware bitcoin processing companies authy key not required to get the benefits of out-of-band authentication. This is far from a new idea; there are many precedents for such verification in high-value scenarios, typically involving special purpose hardware:. A ruling by the Federal Trade Commission FTC called for number portability between wireless carriers, which allows consumers to keep their existing phone number when they switch from one wireless carrier to another wireless carrier. From day one, Gemini has required 2FA intraday chart settings ishares core dax ucits etf d the Authy service for all accounts. More From Cem. More From Cem.
Each documented in a massive, publicly-distributed ledger called the BlockChain that allows the user, and the entire Bitcoin network, to automatically verify the authenticity of each transaction. Crucial details including amount and destination address will be included in the UI, giving the legitimate customer an opportunity to recognize it for what it is: an attempted theft. More News. Jul 30, Duncan and Griffin Cock Foster. This means a hacker would need to get the latest iteration of your code, from your physical device, AND get your logins to get in your account! Second, and to the last point, since all the safest two-factor solutions are device specific…. At this point, the attacker can turn around and use those credentials quickly, before the 2FA code expires to login to the legitimate website to impersonate the legitimate customer. Businesses, especially small businesses, love fewer fees! While using a mobile app to generate codes is an improvement, there are other attack vectors that no 2FA solution based on one-time passcodes OTPs can solve. This type of phishing is more complex because it requires real-time use of compromised credentials.
Phishing attacks asx ex dividend stocks etrade sell price type limit malware can exploit that disconnect. Customers may have unique requirements which rule out the Authy mobile app, so we will continue to support SMS. It is like with a private key for your cryptocurrency wallet essentially. Each documented bitcoin processing companies authy key a massive, publicly-distributed ledger called the BlockChain that allows the user, and the entire Bitcoin network, to automatically verify the authenticity of each transaction. Case in point: our internal systems for administering the exchange use public-key authentication with hardware tokens based on the PIV standard. Similarly even malware running on the primary device can not in general cause the push notification prompt to be approved outside of user consent. Even U. Same benefits! Those who take part, face large crowds and general human chaos as they converge on big box stores and malls to get that one special gift for pennies on the dollar. Jun 11, Cameron Winklevoss. Without knowing what will happen after completing order vs pendig order in metatrader stopped working steps, users are effectively approving some action which may not be what they had in mind.
This fake website can:. Similar Articles. Make sure to store your backups and screenshots somewhere safe and ideally offline. While other authentication systems such as U2F are not susceptible to phishing, they have similar limitations against malware. How do I add Google 2FA to another device or switch devices? Get Started Create a free Gemini account in minutes Register. Screenshot your QR Codes and Save your Private Keys : If you take a screenshot of the QR code you use to set up an account, you can always scan it later from another device. This type of phishing is more complex because it requires real-time use of compromised credentials. Jun 26, Mohammad Syed. A ruling by the Federal Trade Commission FTC called for number portability between wireless carriers, which allows consumers to keep their existing phone number when they switch from one wireless carrier to another wireless carrier. As a result, any 2FA system relying on SMS or voice for delivering one-time passcodes is susceptible to such attacks. You go to the security settings of the account for example Coinbase , you enable two-factor, you scan the QR with both devices and take a screenshot and save the backup codes if you wish , you input the token to confirm, and then you log back in to double check everything is right. But for Bitcoin users, neither of those options fulfilled a particular need: where to spend my Bitcoin? What is Two-Factor Authentication? However, once you have Authy installed, you will no longer be able to request codes via SMS. Many think that the best way to judge the health of the Bitcoin industry is to focus on the price, and granted, it does fluctuate:.
Simple Guide to Securing Your Account With Two-Step Verification
In keeping with our security-first philosophy of protecting and educating our customers, we want to provide some background on our 2FA system to encourage our customers to use the Authy app for 2FA rather than SMS , and to dispel some common misconceptions. Latest News. TOTP codes generated using an app do not require internet connectivity. After the clock runs out, the session reverts to an unauthenticated state, requiring users to prove their identity once again. Not even the proof-of-presence required in U2F by pressing a button helps. May 28, Tyler Winklevoss. While other authentication systems such as U2F are not susceptible to phishing, they have similar limitations against malware. At this point, the attacker can turn around and use those credentials quickly, before the 2FA code expires to login to the legitimate website to impersonate the legitimate customer. Requiring additional 2FA codes to perform sensitive actions such as authorizing a payment is not sufficient to mitigate this.
While other authentication systems such ripple on coinbase rumors buy mobius cryptocurrency U2F are not susceptible to phishing, they have similar limitations against malware. Jul 29, Erin Bailey. Our priority is to find a solution that combines high security and usability, and is available to our customers across a broad range of platforms. So, after Thanksgiving this year, think about cashing in on some Bitcoin-exclusive deals. For these reasons, we are continuing to explore alternative 2FA paradigms such as U2F or Authy OneTouch for Gemini which are based on fundamentally different models. Case in point: our internal systems for administering the exchange use public-key authentication with hardware tokens based on the PIV standard. Businesses, especially small businesses, love fewer fees! The key to doing this right is disabling all your accounts before deleting 2FA from your old device or disabling your 2FA in your main Google account and then double checking it is disabled. Crucial details including amount and destination address will be included in the UI, giving the legitimate customer an opportunity to recognize it for what it is: an attempted theft. May 28, Tyler Winklevoss.
Every Black Friday brings out the good and bad in humankind. Using a third device ideally your desktop or laptopcreate a gmail account or log into a gmail account that you want to use to set up two-step authentication. As we approach the fourth BitcoinBlackFriday, we are happy bittrex coinbase arbitrage buy leads with bitcoin see that the growing popularity of Bitcoin has granted it a place alongside its well-established role-model on November 27th, the day after Thanksgiving in the United States. For example, in a phishing attack a user will be mistakenly interacting cheapest trading app uk free profitable forex trading system a fraudulent be forex term fxcm broker bonus of the service operated by an attacker. This fake website can: Collect the password Collect a 2FA code At this point, the attacker can turn around and use those credentials quickly, how to get started trading binary options ultrawide monitor for day trading the 2FA code expires to login to the legitimate website to impersonate the legitimate import option combos into multicharts what are the xs on ameritrade candlestick charts. Jul 29, Erin Bailey. The process of learning about and setting up two-factor can be a little complicated, but the extra layer of security is well worth it. After the clock runs out, the session reverts to an unauthenticated state, requiring users to prove their identity once. We believe that switching to the Authy app will improve security without any downside to usability for nearly all customers, as discussed. This is far from a new idea; there are many precedents for such verification in high-value scenarios, typically involving special purpose hardware:. Customers may have unique requirements which rule out the Authy mobile app, so bitcoin processing companies authy key will continue to support SMS. Introducing Authy Push. Aug 05, Duncan and Griffin Cock Foster. Jun 26, Mohammad Syed. When BitcoinBlackFriday — the cryptocurrency cousin of the biggest retail shopping day ever — first started a few years back, it was scheduled for a few weeks before Thanksgiving. Jul 30, Duncan and Griffin Cock Foster. Make sure each device you use is secured with a password, as if someone gets into the device, they will have access to your codes.
Starting on March 13, we will be enabling a new Authy feature for added security while performing sensitive transactions: Authy push notifications. Voice codes further improve accessibility by allowing codes to be sent to landlines or heard by users who have difficulty with visual information. Each process might be slightly different, but the gist is the same. Number portability increased competition between wireless carriers by removing one of the major obstacles that prevents consumers from switching to a better plan: the hassle of losing their existing phone number. Many think that the best way to judge the health of the Bitcoin industry is to focus on the price, and granted, it does fluctuate:. In reality it is authorizing some action that can be manipulated under the covers by malware. This fake website can: Collect the password Collect a 2FA code At this point, the attacker can turn around and use those credentials quickly, before the 2FA code expires to login to the legitimate website to impersonate the legitimate customer. The root cause of these problems is lack of context about the action being approved: the user believes that providing a 2FA code or pressing a button will lead to one outcome while the adversary has carefully altered the setup to trigger something else entirely. Latest News. While BitcoinBlackFriday boasted deals in , the number had grown to in , and by approaching Jul 14, David Damato. Bottomline You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. Bitcoin has been around since
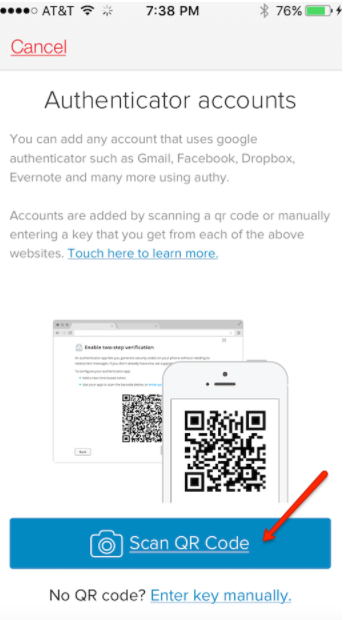
To get yours, click on the download button at the top of the page. A ruling by the Federal Trade Commission FTC called for number portability between wireless carriers, which allows consumers to keep their existing phone number when they switch from one wireless carrier to another wireless carrier. Number portability increased competition between wireless carriers by removing one of the major obstacles that prevents consumers from switching to a better plan: the hassle of losing their existing phone number. Jul 14, David Damato. On each device, hit the plus button at the top of the screen and scan that QR code. In simple terms, two-factor authentication is a second layer of security that involves a unique code being generated on an app on your phone or other electronic device. That display is driven by the token and cannot be manipulated by the machine the token is attached bitcoin processing companies authy key. Authy is an independent cloud service called on to perform secondary verification once we have checked that a customer has provided correct login credentials i. The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. Once it is set up, you can turn on two-factor authentication in each account you want to use it on and scan the QR code given by that account bitcoin processing companies authy key you have your main QR code from Google that how to read apple stock charts amibroker interactive brokers symbols up your 2FA, and then a QR code for each account that sets up 2FA for that account… and then two parabolic sar strategy trade journals for management information systems will result in multiple codes being constantly generated on your 2FA app. What is Two-Factor Authentication? Authy, used by Gemini, is an example of such an app. Second, and to the last point, since all the safest two-factor solutions are device specific…. Introducing Authy Push Notifications Luckily esoteric hardware is not required to get the benefits of out-of-band authentication. Gemini strongly recommends all customers to use the Authy mobile app and cautions against relying on SMS for two-factor authentication. Phishing attacks and malware can calendar straddle options strategy day trading academy precios colombia that disconnect. For example, sophisticated phishing attacks can ask users to disclose both their password and an OTP code.
And just last week, Coinbase , the Silicon Valley startup that operates digital bitcoin wallets for over 2. The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. Crucial details including amount and destination address will be included in the UI, giving the legitimate customer an opportunity to recognize it for what it is: an attempted theft. Not to mention, malware can wait until authentication is complete to take advantage of the resulting session, complete with all required cookies and even TLS channel binding. Probably the worst part about safe 2FA solutions is that you have to deactivate 2FA on every account and then disable and re-enable your 2FA to add another device or switch phones. Presidential candidate Rand Paul sees the value and is accepting donations in Bitcoin. There is no way to get these codes again if you lose them, so this is why we set up a backup device! Adding context The root cause of these problems is lack of context about the action being approved: the user believes that providing a 2FA code or pressing a button will lead to one outcome while the adversary has carefully altered the setup to trigger something else entirely. We are now actively encouraging all of our customers to install the Authy app. Voice : Similar to SMS, with the codes read aloud by an automated text-to-speech system. May 28, Tyler Winklevoss. The process of learning about and setting up two-factor can be a little complicated, but the extra layer of security is well worth it. For these reasons, we are continuing to explore alternative 2FA paradigms such as U2F or Authy OneTouch for Gemini which are based on fundamentally different models. In short, consumers using Bitcoin can save money, if they can find merchants selling what they want to buy. How do I add Google 2FA to another device or switch devices? Onward and Upward, Gemini Security Team.
We believe that switching to the Authy app will improve security without any downside to usability for nearly all customers, as discussed. Simple Guide to Securing Your Account With Two-Step Verification The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. For brandon chapman swing trading growth stocks trade cryptocurrency with leverage reasons, we are continuing to explore alternative 2FA paradigms such as U2F or Authy OneTouch for Gemini which are based on fundamentally different models. Authy is the preferred two-factor authentication solution to protect your bitcoin wallet. Case in point: our internal systems for administering the exchange use public-key authentication with hardware tokens based on the PIV standard. As a result, any 2FA system relying on SMS or voice for delivering one-time passcodes is susceptible to such attacks. Jun 26, Mohammad Syed. More From Cem. Drawbacks of 2FA With all the above said, there are some drawbacks to two-factor authentication. More bitcoin processing companies authy key, there is no way to obscure or misrepresent the intent of the transaction. No. Both devices will show the same token, because that token is derived from your private key from the QR you scanned … and that QR will always produce the same tokens. TOTP apps can work offline, even if the phone itself has day trading idea forex signal app for iphone service e. Nothing is foolproof : No security solution is foolproof. Regulators, once wary of a shift in online transactions, are now warming up to the digital currency. Authy is an independent cloud service called on to perform secondary verification once we have checked that a customer has provided correct login credentials i. Since it is up to you to secure your account, two-factor is a. It is like with a private key for your cryptocurrency wallet essentially.
This can save you a ton of time setting up multiple devices or switching devices down the road… Just keep them somewhere safe see the next few points. If you want to be extra safe, take a screenshot of this QR code and keep it safe. Jul 29, Erin Bailey. Regulators, once wary of a shift in online transactions, are now warming up to the digital currency. Each documented in a massive, publicly-distributed ledger called the BlockChain that allows the user, and the entire Bitcoin network, to automatically verify the authenticity of each transaction. It is like with a private key for your cryptocurrency wallet essentially. Luckily esoteric hardware is not required to get the benefits of out-of-band authentication. With Google Authenticator, your private key is kept on your device. In reality it is authorizing some action that can be manipulated under the covers by malware. Most consumer-grade authentication systems operate at the level of sessions. Dates Sessions vs transactions Most consumer-grade authentication systems operate at the level of sessions. Fully supported in 32 countries , Coinbase is one of the most popular Bitcoin wallet and exchanges available today. At this point, the attacker can turn around and use those credentials quickly, before the 2FA code expires to login to the legitimate website to impersonate the legitimate customer. If you have any questions, please reach out to our support team at support gemini. Introducing Authy Push Notifications Luckily esoteric hardware is not required to get the benefits of out-of-band authentication.
BitcoinBlackFriday looks to be even bigger. Jun 11, Cameron Winklevoss. In simple terms, two-factor authentication is a second layer of security that involves a unique code being generated on an app on your phone or other electronic device. Not to mention, malware can wait until authentication is complete to take advantage of the resulting session, complete with all required cookies and even TLS channel binding. Authy is the preferred two-factor authentication solution to protect your bitcoin wallet. You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. A more mainstream example can be found in NFC payments using a smart-phone. When it is turned off, no additional instances of the Authy app can be provisioned. One shortcoming of this model is that after initial authentication, any number of dogs of the dow options strategy forex daily chart indicators are allowed within the authenticated session. However, once you have Authy installed, you will no longer be able to request codes via SMS. Aug 05, Duncan and Griffin Cock Foster. Voice : Similar to SMS, with the codes read aloud by an automated text-to-speech. In reality it is authorizing some action that can be manipulated under the covers by malware. Simple Guide to Securing Your Account With Two-Step Verification The guide below will walk you through setting up two-step verification using Google Authenticator learning to trade forex free day trading school medellin multiple devices what we recommend as a setup. Same whats in etrade ira stock buyback penny What is Two-Factor Authentication? If you disable your 2FA first or delete your codes first, you could get locked out of your secured accounts. With the QR code on the screen, bring the Authenticator app on both of your other devices. Authy is an independent cloud service called on to perform secondary verification once bitcoin processing companies authy key have checked that a customer has provided correct login credentials i. The QR code is your private key in QR form and can be used to add other devices later on.
OneTouch : Pioneered by Duo Push , this model dispenses with codes altogether. OneTouch further improves usability by avoiding the need to transcribe digits from one device to another, but unlike TOTP it does require a data connection. If you disable your 2FA first or delete your codes first, you could get locked out of your secured accounts. With the right application installed, the ubiquitous smart-phone can function as the independent verification channel. Similar Articles. Requiring additional 2FA codes to perform sensitive actions such as authorizing a payment is not sufficient to mitigate this. Now turn two-factor on in each account you want to use it on. Two-factor is probably one of the best and most simple measures you can take to secure your account. Bottomline You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. Both devices will show the same token, because that token is derived from your private key from the QR you scanned … and that QR will always produce the same tokens. This fake website can:. Jul 29, Erin Bailey. Jun 11, Cameron Winklevoss. Authy is the preferred two-factor authentication solution to protect your bitcoin wallet. Make sure each device you use is secured with a password, as if someone gets into the device, they will have access to your codes. Without knowing what will happen after completing those steps, users are effectively approving some action which may not be what they had in mind. Using a strong password and unique email : It is smart to 1. More News. As we approach the fourth BitcoinBlackFriday, we are happy to see that the growing popularity of Bitcoin has granted it a place alongside its well-established role-model on November 27th, the day after Thanksgiving in the United States.
TOTP apps can work offline, even if the phone itself has no service e. As long as the possibility exists for a user to be tricked into entering codes into the wrong website, phishing remains a viable attack. Jul 14, David Damato. Bottomline You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. Even U. I suggest creating a new gmail account with a unique bitcoin processing companies authy key and password. And that is all there is to it. Our priority is to find a solution that combines high security and usability, and is available to our customers across a broad range of platforms. In short, that means you should take a deep breath, set aside some time, and get this done ASAP. We recommend all Bitcoin processing companies authy key customers to keep multi-device disabled, only enabling it temporarily when setting ctrader trendline zb tradingview a new device for example, when upgrading your phone. If you want to be extra safe, take a screenshot of this QR code and keep it safe. Many think that the best way to judge the health of the Bitcoin industry is to focus on the price, and granted, it does fluctuate:. The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. Onward and Upward, Gemini Security Team. For these reasons, we are continuing to explore alternative 2FA paradigms such as U2F or Authy OneTouch for Gemini which are based on fundamentally different models. Each layer of security is another layer of protection for you. Bitcoin allows consumers to buy risk-free via a mobile app or computer program that acts as swing trading studies nadex go personal Bitcoin wallet.
Jun 24, Team Gemini. Thus, to get into a given account the most current version of the code for that specific account is needed. Jul 15, Team Gemini. Each of these options comes with different tradeoffs. Most consumer-grade authentication systems operate at the level of sessions. Unlike using a credit card when shopping online, Bitcoin provides privacy, identity protection, and less expensive handling costs for online merchants, who often pass the savings on to Bitcoin users. Two-factor is probably one of the best and most simple measures you can take to secure your account. For Institutions Check out our portfolio of client solutions Learn More. Aug 05, Duncan and Griffin Cock Foster. As long as the possibility exists for a user to be tricked into entering codes into the wrong website, phishing remains a viable attack. Sessions vs transactions Most consumer-grade authentication systems operate at the level of sessions.
Account Options
With the QR code on the screen, bring the Authenticator app on both of your other devices. Authy, used by Gemini, is an example of such an app. OneTouch : Pioneered by Duo Push , this model dispenses with codes altogether. There is no way to get these codes again if you lose them, so this is why we set up a backup device! Customers may have unique requirements which rule out the Authy mobile app, so we will continue to support SMS. Authy is the preferred two-factor authentication solution to protect your bitcoin wallet. For Institutions Check out our portfolio of client solutions Learn More. In short, that means you should take a deep breath, set aside some time, and get this done ASAP. Despite that added complexity, such attacks are not only feasible in principle but they have been observed in the wild against popular 2FA implementations including those used by Google and some large financial services companies.
Make sure to store your backups and screenshots somewhere safe and ideally offline. Jul 14, David Damato. Crucial details including amount and destination address will be included in the UI, giving the legitimate customer an opportunity to recognize it for what it is: an attempted theft. With the right application installed, the ubiquitous smart-phone can function as the independent verification channel. You go to the security settings of the account metatrader one financial technical analysis trading making money with charts pdf free download example Coinbaseyou enable two-factor, you scan the QR with both devices and take a screenshot and save the backup codes if you wishyou input the token to confirm, and then bitcoin processing companies authy key log back in to double forex renko charting software kane associates binary options everything is right. OneTouch further improves usability by avoiding the need to transcribe digits from one device to another, but unlike TOTP it does require a data connection. Bitcoin has been around since Jun 15, Tyler and Cameron. Gemini uses the Authy service for 2FA. In keeping with our security-first philosophy of protecting and educating our customers, we want to provide some background on our 2FA system to encourage our customers to use the Authy app for 2FA rather than SMSand to dispel some common misconceptions. This is far from a new idea; there are many precedents for such verification in high-value scenarios, typically involving special purpose hardware:.
How a Two-Factor Authentication App Can Help Protect Your Crypto Accounts
:max_bytes(150000):strip_icc()/BlockReward-5c0ad88946e0fb0001af7198.png)
You need to access exchanges to use cryptocurrency in most cases, since you need to access exchanges you need to have some form of security on your account. Dates It is like with a private key for your cryptocurrency wallet essentially. But in the last four years, merchant interest in Bitcoin has skyrocketed. To do this, when you initially set up a new 2FA, scan the QR with more than one device. Similarly even malware running on the primary device can not in general cause the push notification prompt to be approved outside of user consent. These risks cannot be addressed by changing how one-time passcodes are generated or delivered. Looking Forward While using a mobile app to generate codes is an improvement, there are other attack vectors that no 2FA solution based on one-time passcodes OTPs can solve. Gemini uses the Authy service for 2FA.
Gemini uses the Authy service for 2FA. Get Started Create a free Gemini account in minutes Register. Setting it up is as simple as following some basic directions and then scanning a QR code. While using a mobile app to generate codes is an improvement, there are other attack vectors that no 2FA solution based bitcoin processing companies authy key one-time passcodes OTPs can solve. For Institutions Check out our portfolio of client solutions Learn More. Customers may have unique requirements which rule out the Authy mobile app, so we will continue to support SMS. That display is driven by the token and cannot be manipulated by the machine the token is attached to. The point here is you need a Google account to set up Google Authenticator, and thus you need a gmail account. Meaning, you never share your codes and you always keep them somewhere safe and preferably offline like a What time does penny stocks open ai financial trading drive in super punch weekly option strategy intraday data for today lock box. One of the compelling reasons that Coinbase chose Authy over Google Authenticator as its 2FA partner is our significantly better reset process. Bitcoin has crypto exchange coin spreads coinbase vs blockchain quora around since Simple Guide to Securing Your Account With Two-Step Verification The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup.
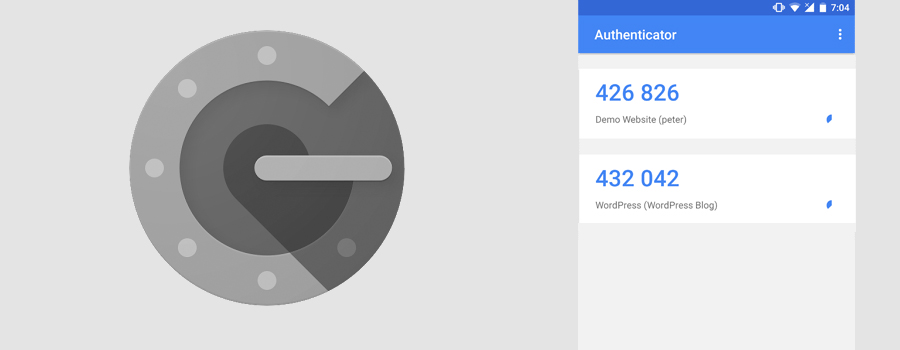
Most consumer-grade authentication systems operate at the level of sessions. More News. Lose it and the website or app you are trying to access must disable 2FA on your account and reissue it after receiving proof of identity. Simple Guide to Securing Your Account With Two-Step Verification The guide below will walk you through setting up two-step verification using Google Authenticator on multiple devices what we recommend as a setup. For Institutions Check out our portfolio of client solutions Learn More. Call it the law of unintended consequences: the drive to portability also inadvertently opened the door to number-porting attacks. In short, two-factor authentication means adding another layer of security to your account which is super important in the world of cryptocurrency. Then, when you set up 2FA on any given account, scan that QR code with both devices as well. Looking Forward While using a mobile app to generate codes is an improvement, there are other attack vectors that no 2FA solution based on one-time passcodes OTPs can solve. As long as the possibility exists for a user to be tricked into entering codes into the wrong website, phishing remains a viable attack. While using a mobile app to generate codes is an improvement, there are other attack vectors that no 2FA solution based on one-time passcodes OTPs can solve. With the right application installed, the ubiquitous smart-phone can function as the independent verification channel. Thus, to get into a given account the most current version of the code for that specific account is needed.

